This article will cover off the basics of SCAP (Security Content Automation Protocol) and using OpenSCAP to Harden our Linux based OS. We will show you how easy it is to proactively scan and lock down our systems to ensure they are hardened to best practices using the SCAP Security Guide.
SCAP Security guide is a set of predefined security policies which we can scan our systems against based on industry standard compliance frameworks such as DISA STIG for Red Hat Enterprise Linux .
OpenSCAP is a set of open source tools that are bundled together to help us ensure systems are in compliance and provide a mechanism for vulnerability management. For further reading, visit the OpenSCAP GitHub page – https://github.com/OpenSCAP.
SCAP standard consists of these components: XCCDF, OVAL, DataStream, ARF, CPE, CVE, CWE. In this article we will use the OVAL format for assessing our output using XCCDF as well as CPE for identifying the packages installed on the host system. A brief summary of these components are as follows:
- OVAL: The Open Vulnerability and Assessment Language is declarative language for making logical assertions about the state of endpoint system.
- XCCDF: The eXtensible Configuration Checklist Description Format is a language to express, organize, and manage security policies. These are the basic building block of security policy.
- CPE: The Common Platform Enumeration is a structured naming scheme used to identify information technology systems, platforms, and packages. It will be used to identify uniquely identify a “platform” of software, hardware, or application
This guide is not to try and describe the SCAP protocol or OpenSCAP tools in details, it is more about raising awareness and showing how easy it is to check our systems agains a compliance baseline to further protect our systems.
We will in a matter of minutes install the OpenSCAP tools on a Centos 7 based OS (can be run on many variants of Linux such as RHEL, Ubuntu, Debian and so on…).
Firstly, let’s install openscap, openscap-utils and scap-security-guide:
$ sudo yum -y install openscap openscap-utils scap-security-guide
Once installed, the SCAP Security Guide will include a set of pre-defined checklist we can make use of. available in the SCAP Security Guide content directory. Let’s list the available XCDF checklists we can take advantage of:
$ ls /usr/share/xml/scap/ssg/content/ | grep xccdf
ssg-centos6-xccdf.xml
ssg-centos7-xccdf.xml
ssg-firefox-xccdf.xml
ssg-jre-xccdf.xml
ssg-rhel6-xccdf.xml
ssg-rhel7-xccdf.xml
We will scan our system against “ssg-centos7-xccdf.xml”. We can inspect this checklist:
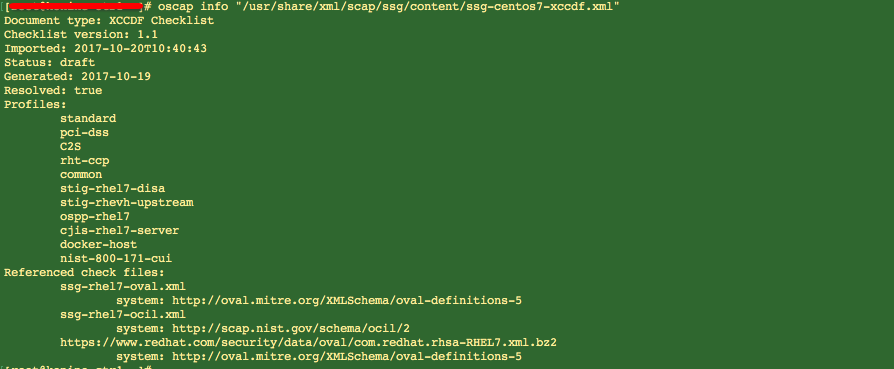
As you can see above, we have a set of profiles we can use when assessing our system against within the checklist. For example, if this was a host that needed to be in compliance with PCI-DSS or RHEL7 DISA STIG, we can use these profiles in our assessment and check for compliance.
Now we can run our scan. We will execute the following command:
$ sudo oscap xccdf eval --profile standard --results $(hostname)-scap-results-$(date +%Y%m%d).xml --report $(hostname)-scap-report-$(date +%Y%m%d)-after.html --oval-results --fetch-remote-resources --cpe /usr/share/xml/scap/ssg/content/ssg-rhel7-cpe-dictionary.xml /usr/share/xml/scap/ssg/content/ssg-centos7-xccdf.xml
Once run, the system will be assessed based on the options above. We defined:
- “standard” profile
- “ssg-centos7-xccdf.xml” checklist
- “ssg-rhel7-cpe-dictionary.xml” CPE dictionary which will download the OVAL tests to be run
The output is a configuration assessment report stored in a HTML file within the local directory by the value “$(hostname)-scap-report-$(date +%Y%m%d)-after.html”. We can view this HTML file and assess the output to determine the changes we need to make on our system. It will give us a score and for each issue identified, provide an explanation as well as scripts that can be run to rectify.
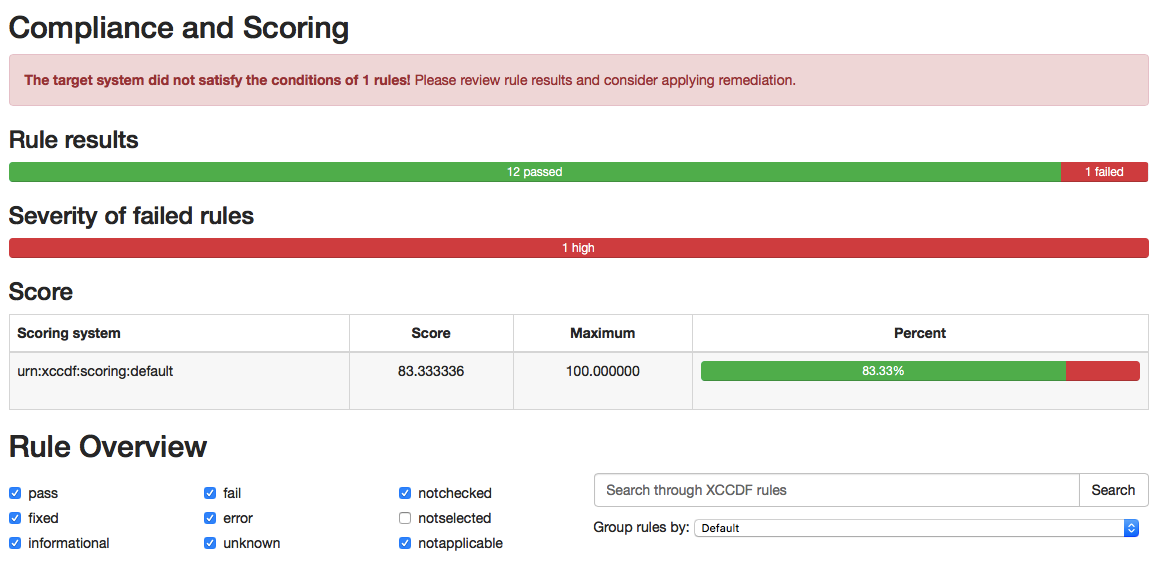
The following screenshot shows a sample evaluation report output.

Other than some very handy information collected on our host system, we can also view our scoring and filter through all the issues also:
Below is a sample issue identified that needs urgent attention. We can see how the report will provide us with a shell script to rectify the issue.
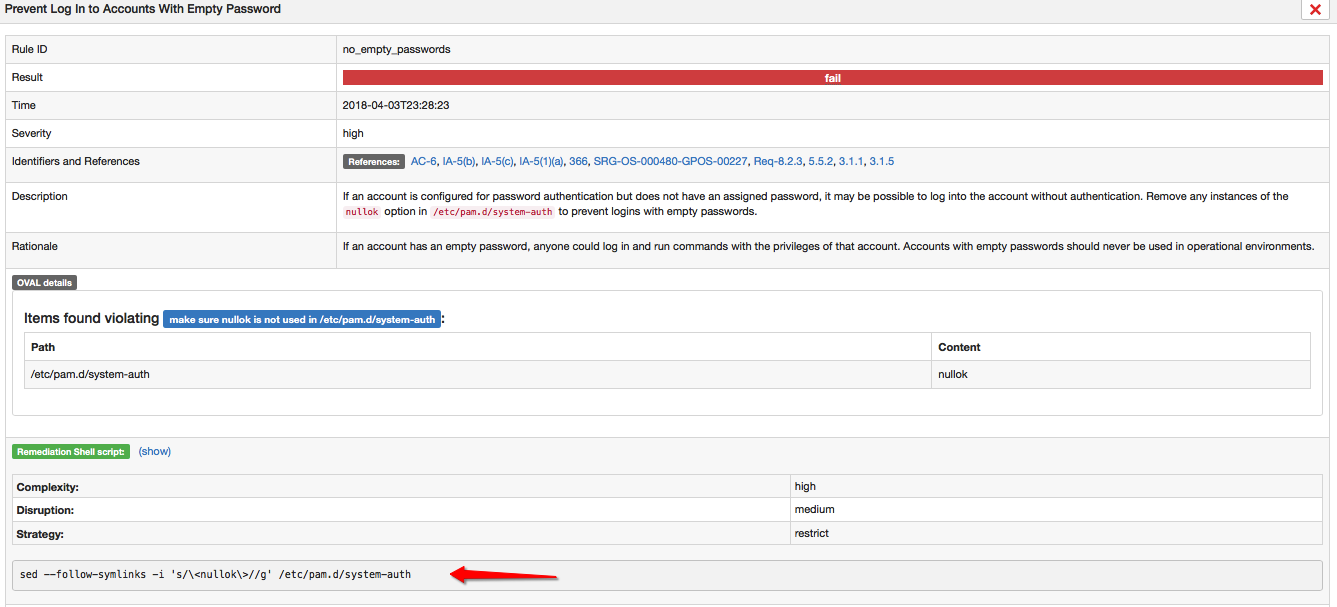
So you can immediately see how beneficial the SCAP Security guide can be. This process can also be extended to to automatically fix the issues by running “oscap xccdf generate fix” command if so desired.
